Authentication
X509 Certs, Kubectl, ServiceAccount
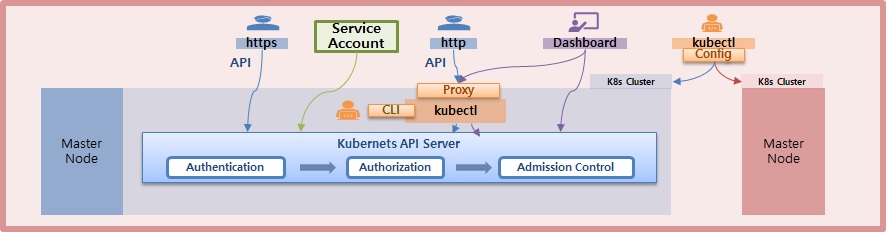
1. X509 Client Certs
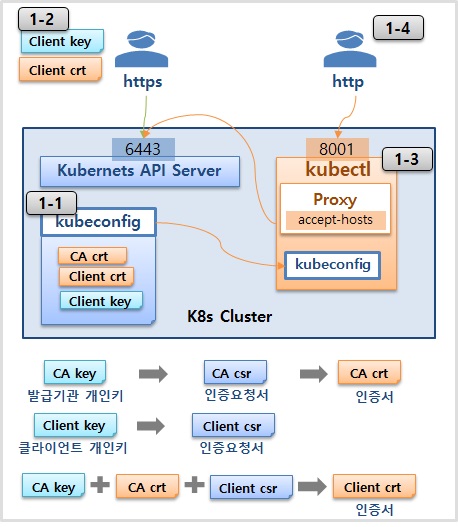
1-1) kubeconfig 인증서 확인
Path : /etc/kubernetes/admin.conf
cluster.certificate-authority-data : CA.crt (Base64)
user.client-certificate-data: Client.crt (Base64)
user.client-key-data: Client.key (Base64)
grep 'client-certificate-data' /etc/kubernetes/admin.conf | head -n 1 | awk '{print $2}' | base64 -d
grep 'client-key-data' /etc/kubernetes/admin.conf | head -n 1 | awk '{print $2}' | base64 -d
1-2) Https API (Client.crt, Client.key)
# case1) postman
https://192.168.56.30:6443/api/v1/nodes
Settings > General > SSL certificate verification > OFF
Settings > Certificates > Client Certificates > Host, CRT file, KEY file
# case2) curl
curl -k --key ./Client.key --cert ./Client.crt https://192.168.56.30:6443/api/v1/nodes# case1) postman
https://192.168.0.30:6443/api/v1/nodes
Settings > General > SSL certificate verification > OFF
Settings > Certificates > Client Certificates > Host, CRT file, KEY file
# case2) curl
curl -k --key ./Client.key --cert ./Client.crt https://192.168.0.30:6443/api/v1/nodes1-3) kubectl config 세팅
# kubeadm / kubectl / kubelet 설치
yum install -y --disableexcludes=kubernetes kubelet-1.27.2-0.x86_64 kubeadm-1.27.2-0.x86_64 kubectl-1.27.2-0.x86_64
# admin.conf 인증서 복사
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
# Kubectl Proxy 띄우기
nohup kubectl proxy --port=8001 --address=192.168.56.30 --accept-hosts='^*$' >/dev/null 2>&1 &# kubeadm / kubectl / kubelet 설치
yum install -y --disableexcludes=kubernetes kubeadm-1.15.5-0.x86_64 kubectl-1.15.5-0.x86_64 kubelet-1.15.5-0.x86_64
# admin.conf 인증서 복사
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
# Kubectl Proxy 띄우기
nohup kubectl proxy --port=8001 --address=192.168.0.30 --accept-hosts='^*$' >/dev/null 2>&1 &1-4) HTTP API 호출 (Proxy)
# case1) postman
http://192.168.56.30:8001/api/v1/nodes
# case2) curl
curl http://192.168.56.30:8001/api/v1/nodes# case1) postman
http://192.168.0.30:8001/api/v1/nodes
# case2) curl
curl http://192.168.0.30:8001/api/v1/nodes2. kubectl
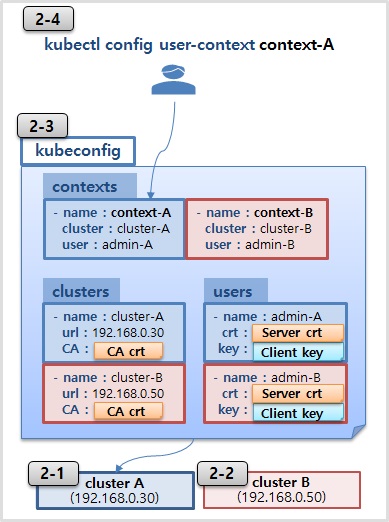
필수 확인사항!
해당 실습을 해보기 위해선 새로운 클러스터를 추가로 설치해야 합니다. 최초 클러스터 구축 가이드를 가지고 IP만 변경해서 다른 클러스터를 하나를 더 설치하고 이때 자원이 부족하게 될 수 있으니 Master만 설치 됩니다.(기존 클러스터 = cluster-a, 새 클러스터 = cluster-b)
새 클러스터(cluster-b) 구축
// 폴더 생성
C:\Users\사용자>mkdir k8s2
C:\Users\사용자>cd k8s2
// Vagrant 스크립트 다운로드
C:\Users\사용자\k8s2> curl -O https://kubetm.github.io/yamls/k8s-install/auth/Vagrantfile
C:\Users\사용자>vagrant up
2-1) Cluster A kubeconfig
path : /etc/kubernetes/admin.conf
2-2) Cluster B kubeconfig
path : /etc/kubernetes/admin.conf
2-3) kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1KVEUtLS0tLQo=
server: https://192.168.0.30:6443
name: cluster-a
- cluster:
certificate-authority-data: LS0tLS1KVEUtLS0tLQo=
server: https://192.168.0.50:6443
name: cluster-b
contexts:
- context:
cluster: cluster-a
user: admin-a
name: context-a
- context:
cluster: cluster-b
user: admin-b
name: context-b
current-context: context-a
kind: Config
preferences: {}
users:
- name: admin-a
user:
client-certificate-data: LS0tLS1KVEUtLS0tLQo=
client-key-data: LS0tLS1KVEUtLS0tLQo=
- name: admin-b
user:
client-certificate-data: LS0tLS1KVEUtLS0tLQo=
client-key-data: LS0tLS1KVEUtLS0tLQo=
2-4) kubectl CLI
kubectl download : https://kubernetes.io/docs/tasks/tools/install-kubectl/
windows
curl -LO https://storage.googleapis.com/kubernetes-release/release/v1.18.0/bin/windows/amd64/kubectl.exe
C:\Users\taemin
kubectl config use-context context-a
kubectl get nodes
3. Service Account
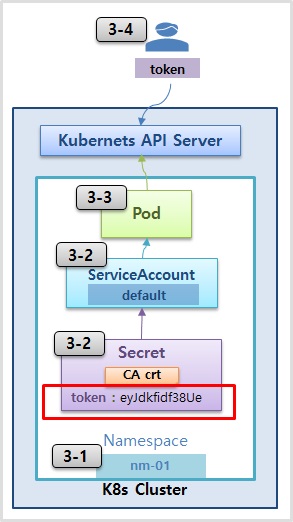
3-1) Namespace
kubectl create ns nm-01
3-2) ServiceAccount & Secret 확인
kubectl describe -n nm-01 serviceaccounts
kubectl describe -n nm-01 secrets
3-3) Pod
cat <<EOF | kubectl create -f -
apiVersion: v1
kind: Pod
metadata:
name: pod-1
namespace: nm-01
labels:
app: pod
spec:
containers:
- name: container
image: kubetm/app
EOF
3-4) Https API 호출 (Token)
# case1) http
# [header] Authorization : Bearer TOKEN
https://192.168.56.30:6443/api/v1
https://192.168.56.30:6443/api/v1/namespaces/nm-01/pods/
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.56.30:6443/api/v1
curl -k -H "Authorization: Bearer TOKEN" https://192.168.56.30:6443/api/v1/namespaces/nm-01/pods/# case1) http
# [header] Authorization : Bearer TOKEN
https://192.168.0.30:6443/api/v1
https://192.168.0.30:6443/api/v1/namespaces/nm-01/pods/
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.0.30:6443/api/v1
curl -k -H "Authorization: Bearer TOKEN" https://192.168.0.30:6443/api/v1/namespaces/nm-01/pods/