Authorization
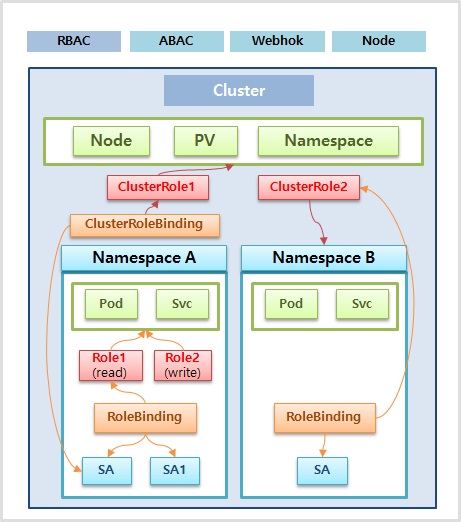
RBAC, Role, RoleBinding
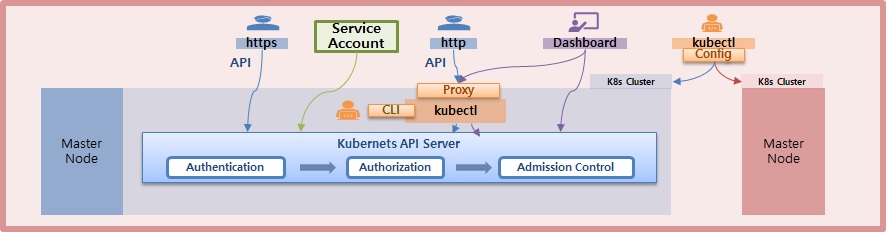
1. 자신의 Namespace 내에 Pod들만 조회할 수 있는 권한
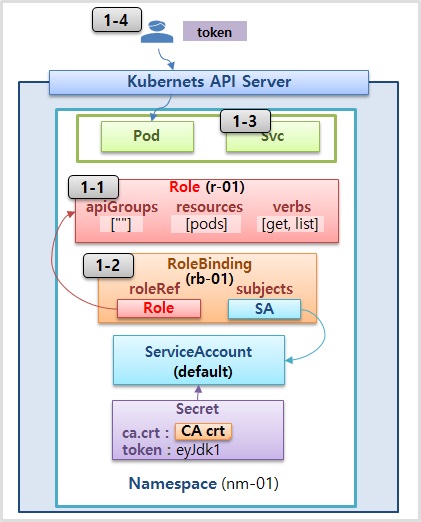
1-1) Role
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: r-01
namespace: nm-01
rules:
- apiGroups: [""]
verbs: ["get", "list"]
resources: ["pods"]
1-2) RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: rb-01
namespace: nm-01
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: r-01
subjects:
- kind: ServiceAccount
name: default
namespace: nm-01
1-3) Service
apiVersion: v1
kind: Service
metadata:
name: svc-1
namespace: nm-01
spec:
selector:
app: pod
ports:
- port: 8080
targetPort: 8080
필독! Secret를 꼭 만들어 주세요
1.24 버전 이후 부터 보안 강화로 serviceAccount에 대해서 자동으로 Secret이 만들어 지지 않습니다. 그래서 필요시 수동으로 만들어야 되요.1-3) Secret
apiVersion: v1
kind: Secret
metadata:
namespace: nm-01
name: default-token
annotations:
kubernetes.io/service-account.name: default
type: kubernetes.io/service-account-token
1-4) Https API 호출 (Token)
# case1) postman
# [header] Authorization : Bearer TOKEN
https://192.168.56.30:6443/api/v1/namespaces/nm-01/pods/
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.56.30:6443/api/v1/namespaces/nm-01/pods/# case1) postman
# [header] Authorization : Bearer TOKEN
https://192.168.0.30:6443/api/v1/namespaces/nm-01/pods/
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.0.30:6443/api/v1/namespaces/nm-01/pods/2. 모든 Namespace 내에 Object들에 대해 모든 권한을 부여
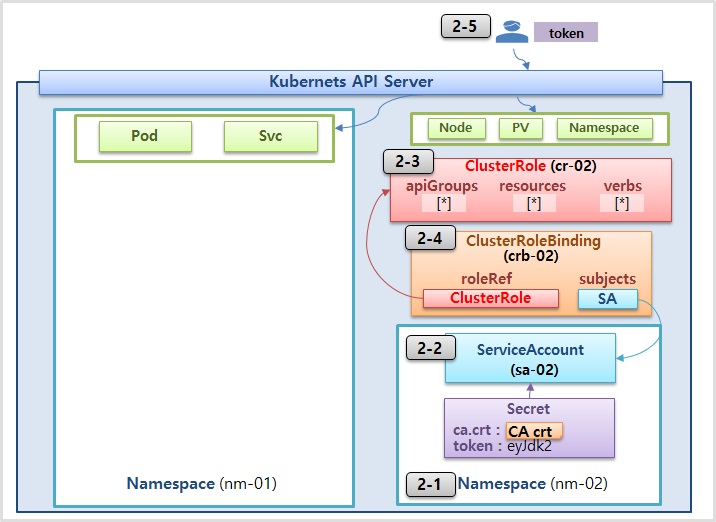
2-1) Namespaces
apiVersion: v1
kind: Namespace
metadata:
name: nm-02
2-2) ServiceAccount
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa-02
namespace: nm-02
필독! Secret를 꼭 만들어 주세요
1.24 버전 이후 부터 보안 강화로 serviceAccount에 대해서 자동으로 Secret이 만들어 지지 않습니다. 그래서 필요시 수동으로 만들어야 되요.2-2) Secret
apiVersion: v1
kind: Secret
metadata:
namespace: nm-02
name: sa-02-token
annotations:
kubernetes.io/service-account.name: sa-02
type: kubernetes.io/service-account-token
2-3) ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cr-02
rules:
- apiGroups: ["*"]
verbs: ["*"]
resources: ["*"]
2-4) ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: rb-02
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cr-02
subjects:
- kind: ServiceAccount
name: sa-02
namespace: nm-02
2-5) Https API 호출 (Token)
# case1) postman
# [header] Authorization : Bearer TOKEN
https://192.168.56.30:6443/api/v1/namespaces/nm-01/service
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.56.30:6443/api/v1/namespaces/nm-01/service# case1) postman
# [header] Authorization : Bearer TOKEN
https://192.168.0.30:6443/api/v1/namespaces/nm-01/service
# case2) curl
curl -k -H "Authorization: Bearer TOKEN" https://192.168.0.30:6443/api/v1/namespaces/nm-01/serviceReferenece
Kubernetes
- Using RBAC Authorization : https://kubernetes.io/docs/reference/access-authn-authz/rbac/
- Review Your Request Attributes : https://kubernetes.io/docs/reference/access-authn-authz/authorization/#review-your-request-attributes